博客一直以来流量都挺大,也懒得管,基本上1天跑5个G左右,这还只是文本(
html),因为图片/js/css做了分流,一天5个G左右的网络流量,那要支持多少IP访问,然而并没有那么多的IP来访问本博客,今天看了一眼,2天21小时跑了12G流量,索性查一下问题出在哪里。

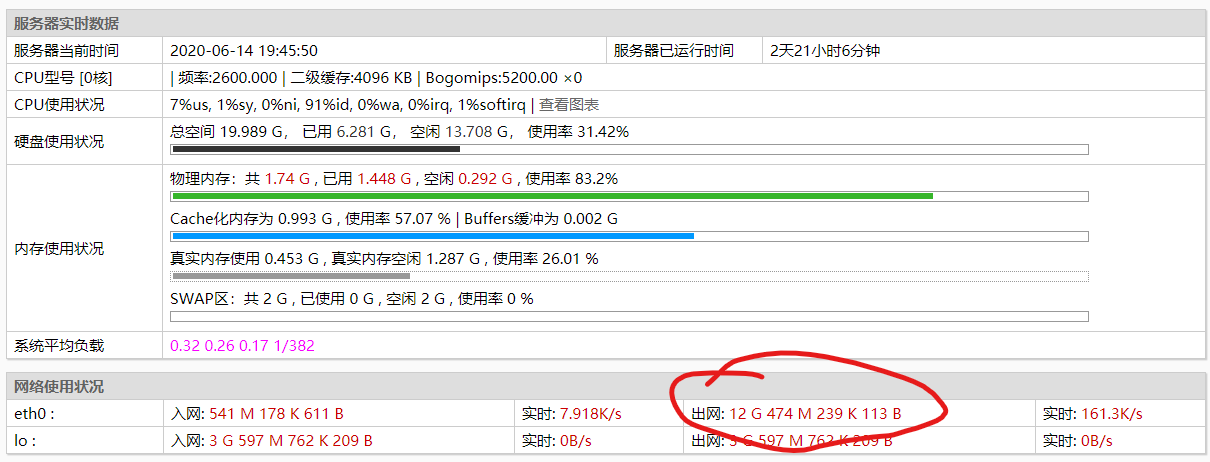
1、排查思路:服务器被入侵沦为肉鸡往外发包、SSH爆破、nginx被扫描、其他进程比如zabbix等服务器监控进程
2、先查看有无异常进程:ps -ef 【排除】
[root@instance-20190918-1225 ~]# ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 Jun12 ? 00:00:14 /usr/lib/systemd/systemd --switched-root --system --deserialize 17
root 2 0 0 Jun12 ? 00:00:00 [kthreadd]
root 3 2 0 Jun12 ? 00:00:00 [rcu_gp]
root 4 2 0 Jun12 ? 00:00:00 [rcu_par_gp]
root 6 2 0 Jun12 ? 00:00:00 [kworker/0:0H-kblockd]
root 8 2 0 Jun12 ? 00:00:00 [mm_percpu_wq]
root 9 2 0 Jun12 ? 00:00:44 [ksoftirqd/0]
root 10 2 0 Jun12 ? 00:00:49 [rcu_sched]
3、先排查ssh爆破:cat /var/log/secure |grep failed |grep wc -l 可以看出爆破很少 【排除】
4、排查nginx日志 awk '{print $1}' /var/log/nginx/access.log |sort -n|uniq -c|sort -rn|head ,可以看出IP【216.244.66.248】访问最多 【定位问题所在】
[root@instance-20190918-1225 ~]# awk '{print $1}' /var/log/nginx/access.log |sort -n|uniq -c|sort -rn|head
12 216.244.66.248
2 111.206.198.38
1 66.249.79.170
1 66.249.79.123
1 66.249.79.121
1 54.36.148.80
1 54.36.148.125
1 54.36.148.117
1 46.229.168.161
5、排查IP 【216.244.66.248】访问的内容,可以看出【216.244.66.248】是一个bot的IP地址
[root@instance-20190918-1225 ~]# cat /var/log/nginx/access.log |grep 216.244.66.248
216.244.66.248 - - [14/Jun/2020:20:03:21 +0800] "GET /feed/archives/1341/ HTTP/1.1" 301 cost:0.092 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:03:25 +0800] "GET /feed/archives/1362/ HTTP/1.1" 301 cost:0.102 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:03:30 +0800] "GET /feed/archives/733/ HTTP/1.1" 301 cost:0.097 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:04:05 +0800] "GET /271.html/?paged=16 HTTP/1.1" 301 cost:0.198 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:04:45 +0800] "GET /?tag=%E6%9C%8D%E5%8A%A1%E5%99%A8&paged=5 HTTP/1.1" 301 cost:0.106 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:06:57 +0800] "GET /feed/atom/?paged=10 HTTP/1.1" 301 cost:0.161 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
216.244.66.248 - - [14/Jun/2020:20:45:06 +0800] "GET /1393.html/?paged=2 HTTP/1.1" 301 cost:0.157 0 "-" "Mozilla/5.0 (compatible; DotBot/1.1; http://www.opensiteexplorer.org/dotbot, help@moz.com)" "-"
6、用firewalld禁用IP【216.244.66.248】
[root@instance-20190918-1225 ~]# firewall-cmd --permanent --add-rich-rule="rule family=ipv4 source address=216.244.66.248 reject"
[root@instance-20190918-1225 ~]# firewall-cmd --list-rich-rules
rule family="ipv4" source address="216.244.66.248" reject
解除禁用的IP 216.244.66.248
[root@instance-20190918-1225 ~]#
firewall-cmd --permanent --add-rich-rule="rule family=ipv4 source address=216.244.66.248 reject"








还没有任何评论,你来说两句吧